 Nowadays, information are provided through diverse network channels and, above all, their diffusion occurs in an always faster and pervasive manner Social Networks (SN) plays a crucial role in distributing, in an uncontrolled way, news, opinions, media contents and so on, and can basically contribute to spread information that sometimes are untrue and misleading.
Nowadays, information are provided through diverse network channels and, above all, their diffusion occurs in an always faster and pervasive manner Social Networks (SN) plays a crucial role in distributing, in an uncontrolled way, news, opinions, media contents and so on, and can basically contribute to spread information that sometimes are untrue and misleading.
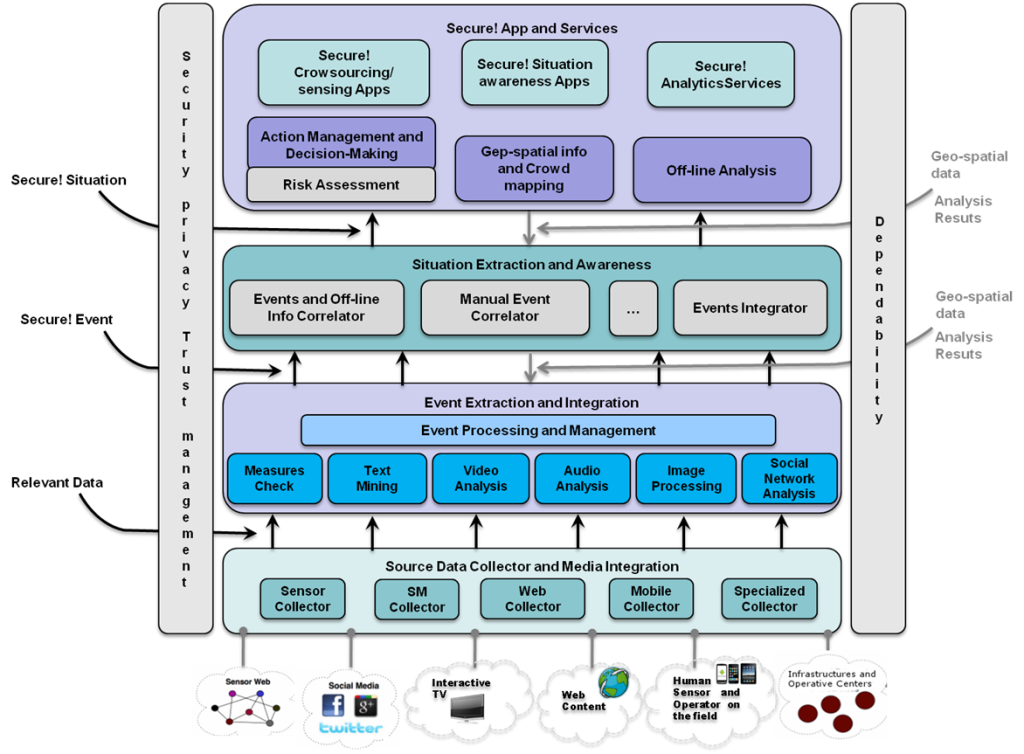
In this framework, an integrated assessment of the trustworthiness of the information that is delivered is claimed from different sides. Research activity has been carried on this hot and challenging topic; in particular within the project SECURE!, it has been studied and developed an infrastructure which, by resorting at diverse technological tool based on image forensics, source reputation analysis, Twitter message trend analysis, web source retrieval, etc., provides an integrated and broad spectrum event assessment.
- “Image Origin Classification based on Social Network Provenance,” in IEEE Transactions on Information Forensics and Security , vol.PP, no.99, pp.1-1 doi: 10.1109/TIFS.2017.2656842.Recognizing information about the origin of a digital image has been individuated as a crucial task to be tackled by the image forensic scientific community. Understanding something on the previous history of an image could be strategic to address any successive assessment to be made on it: knowing the kind of device used for acquisition or, better, the model of the camera could focus investigations in a specific direction. Sometimes just revealing that a determined post-processing such as an interpolation or a filtering has been performed on an image could be of fundamental importance to go back to its provenance. This paper locates in such a context and proposes an innovative method to inquire if an image derives from a social network and, in particular, try to distinguish from which one has been downloaded. The technique is based on the assumption that each social network applies a peculiar and mostly unknown manipulation that however leaves some distinctive traces on the image; such traces can be extracted to feature every platform. By resorting at trained classifiers, the presented methodology is satisfactorily able to discern different social network origin. Experimental results carried out on diverse image datasets and in various operative conditions witness that such a distinction is possible. In addition, the proposed method is also able to go back to the original JPEG quality factor the image had before being uploaded on a social network.
- Datasets:
social_UCID dataset
social_PUBLIC dataset - [new] social UCID multiple dataset
- If you use these datasets, please cite the paper:
R. Caldelli; R. Becarelli; I. Amerini, “Image Origin Classification based on Social Network Provenance,” in IEEE Transactions on Information Forensics and Security , vol.PP, no.99, pp.1-1 doi: 10.1109/TIFS.2017.2656842.
(link http://ieeexplore.ieee.org/document/7829345/)
