The question of trustworthiness of digital image forensic arises because most publications still lack rigorous discussions of robustness against counterfeiters.
Forensic methods might benefit from research on countermeasures in a similar way as reasoning about attacks in multimedia security in general is useful to improve security. In this sense attacks on image forensic algorithms can be understood as schemes to mislead the detection methods. In general, such attacks can be assigned to one of the following three objectives: the camouflage of malicious post-processing or tampering of an image, the suppression of correct image origin identification and furthermore the forgery of image origin.
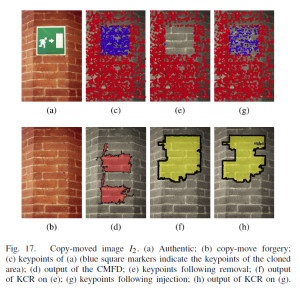
Forensic Analysis of SIFT Keypoint Removal and Injection
Attacks capable of removing SIFT keypoints from images have been recently devised with the intention of compromising the correct functioning of SIFT-based copy–move forgery detection. To tackle with these attacks, we have realized three novel forensic detectors for the identification of images whose SIFT keypoints have been globally or locally removed. The detectors look for inconsistencies like the absence or anomalous distribution of keypoints within textured image regions.
We first validate the methods on state-of-the-art keypoint removal techniques, then we further assess their robustness by devising a counter-forensic attack injecting fake SIFT keypoints in the
attempt to cover the traces of removal. We apply the detectors to a practical image forensic scenario of SIFT-based copy-move forgery detection, assuming the presence of a counterfeiter who resorts to keypoint removal and injection to create copy–move forgeries that successfully elude SIFT-based detectors but are in turn exposed by the newly proposed tools.